From Cloud Chaos to Full Control — Automating Your Open-Source HCI You don’t realize you’ve outgrown the cloud — until you do. The first signs? Your object storage usage hits 100+ TB. Monthly bills creep into four-digit territory. And suddenly, that “convenient” cloud setup feels more like a cage. That’s when building your own open-source […]
Introduction If you’re deploying OpenStack, the question of storage isn’t if—it’s how much pain you’re willing to endure.Choosing the right Ceph storage backend for OpenStack is often the difference between a stable deployment and ongoing headaches. We’ve worked with OpenStack clouds of all sizes—from small dev environments to enterprise-grade clusters with thousands of VMs—and time […]
If you’re evaluating how to build or manage your own S3-compatible object storage, you’re not alone. Even major cloud providers like DigitalOcean made that shift — and chose Ceph, one of the most powerful (and complex) open-source storage platforms available. This wasn’t a decision made lightly. It came after careful technical evaluation and strategic forecasting. […]
Introduction In the fast-evolving landscape of Kubernetes, choosing the right persistent storage backend is crucial for performance, scalability, and operational efficiency. This blog post dives into four widely-used open-source storage solutions — Ceph, GlusterFS, Longhorn, and OpenEBS — and compares them using real-world benchmarks, community feedback, and a technical deep dive into deployment, observability, disaster […]
aws s3 to ceph rgw migration illustration with data bucket and arrow
Introduction At Kubedo, we help our clients build sustainable, scalable, and secure infrastructure using open source technologies. This case study outlines how one of our European SaaS customers transitioned from Zendesk to an open source helpdesk stack — powered by Zammad, Ceph, Kubernetes, and Checkmk. The result: a 90% reduction in annual costs, improved SLA […]
A real-world comparison of Ceph and MinIO for S3-compatible object storage. Analyze open-source licensing, performance benchmarks, and total cost breakdowns.
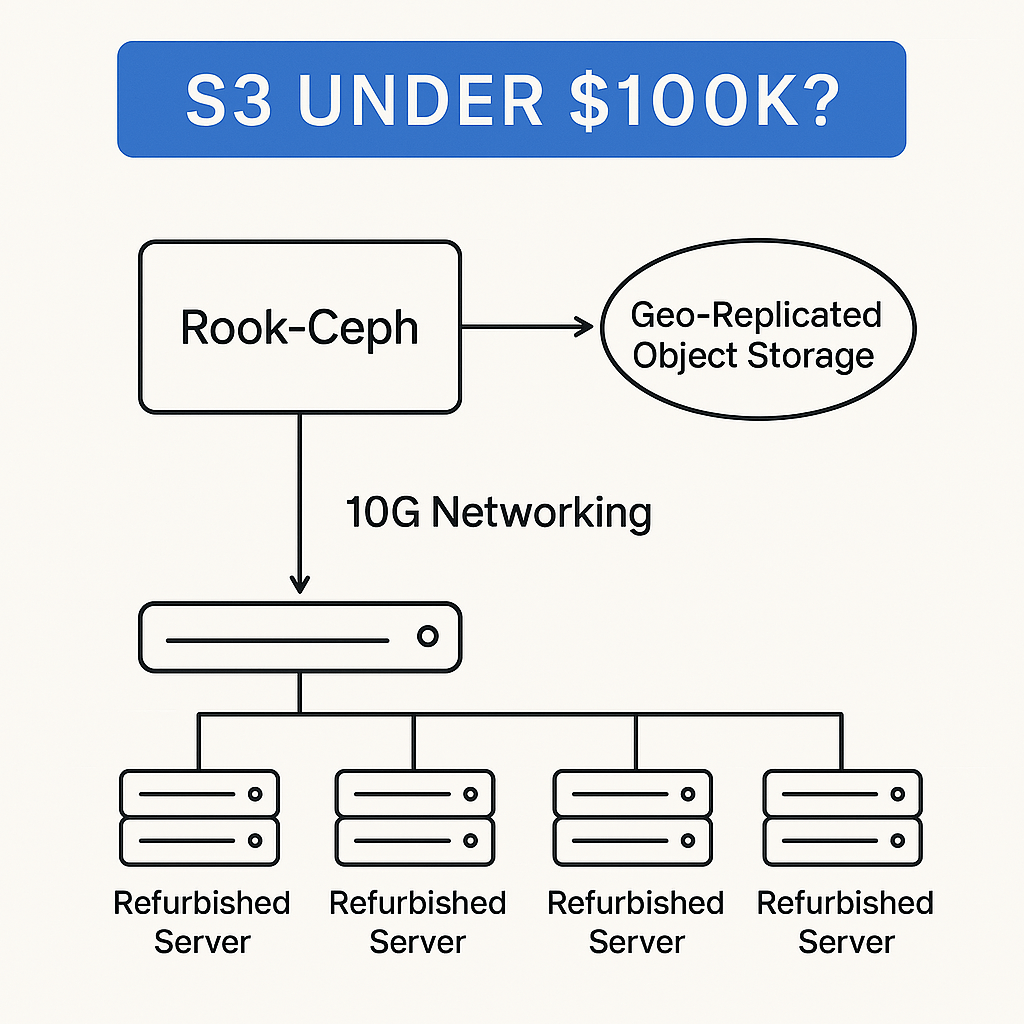
Discover how Rook-Ceph offers a cost-effective, open-source alternative to Amazon S3. Learn how to reduce cloud storage costs, deploy on-prem object storage, and achieve geo-replication with Kubernetes-native tools.
After Broadcom’s acquisition of VMware, many are questioning their allegiance to the platform, considering alternative solutions in light of potential changes. The acquisition has prompted a reevaluation of VMware’s value proposition, leading organizations to explore new options for their virtualization needs. Amidst uncertainty, businesses are weighing their options carefully, contemplating a shift away from VMware in search of more stable and cost-effective alternatives
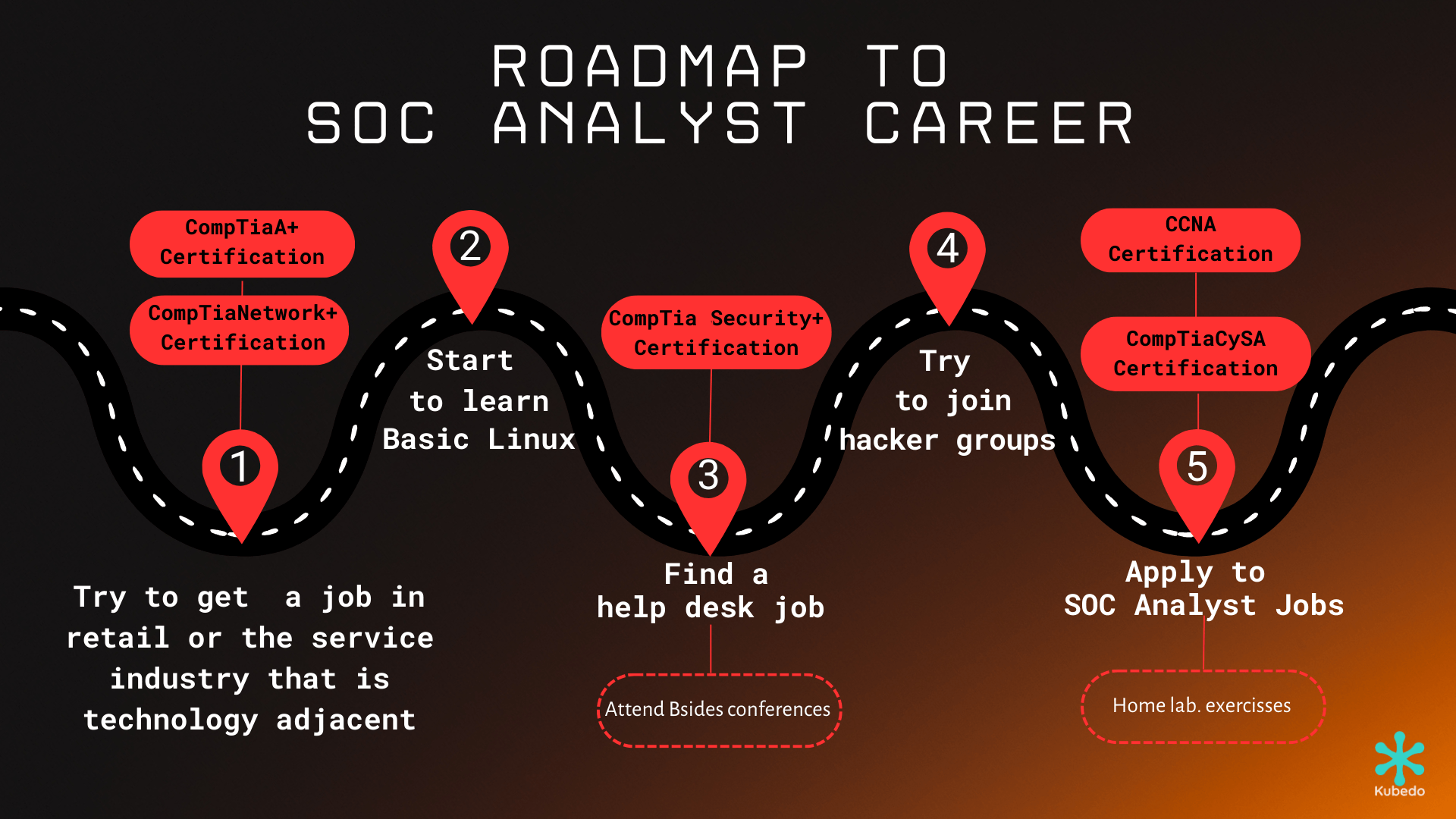
Embarking on a career in cybersecurity may seem like navigating uncharted waters, especially if you’ve never dipped your toes into the vast sea of technology before. This step-by-step guide is your compass, designed to lead you through the intricacies of the IT landscape and mold you into a sought-after Security Operations Center (SOC) analyst. So, buckle up, as we navigate this roadmap together, taking realistic pit stops over the next 3 to 5 years.