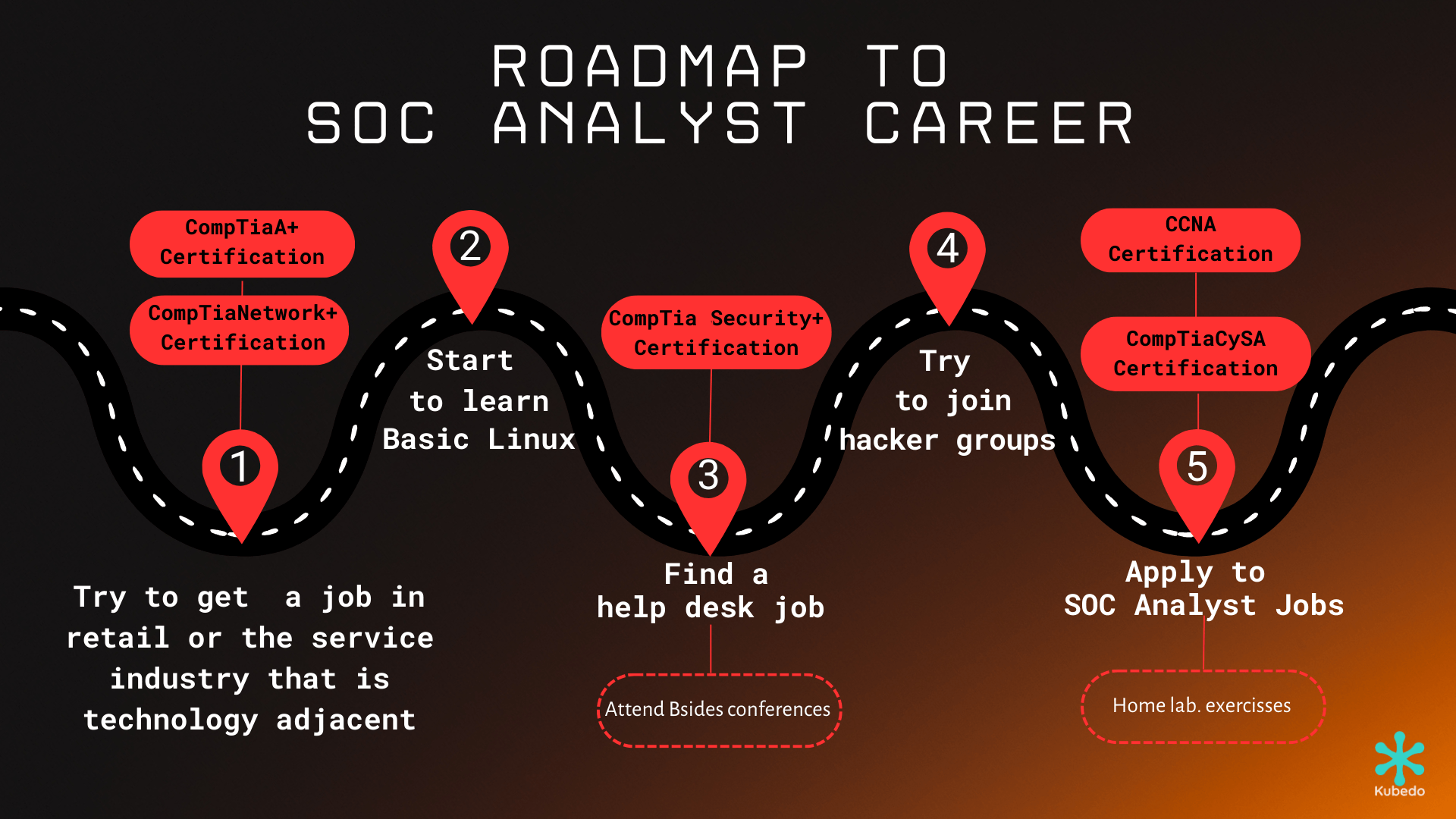
Embarking on a career in cybersecurity may seem like navigating uncharted waters, especially if you’ve never dipped your toes into the vast sea of technology before. This step-by-step guide is your compass, designed to lead you through the intricacies of the IT landscape and mold you into a sought-after Security Operations Center (SOC) analyst. So, buckle up, as we navigate this roadmap together, taking realistic pit stops over the next 3 to 5 years.
Secure your Kubernetes ecosystem with best-in-class strategies and managed IT services. Explore the importance of authentication, authorization, and network policies for containerized applications. Discover how our comprehensive guide ensures optimal safety and performance for your cloud-native infrastructure
In today’s digital age, businesses of all sizes are vulnerable to cyber attacks. Cybersecurity refers to the practice of protecting devices, networks, and sensitive information from unauthorized access, theft, and damage caused by malicious cyber threats such as viruses, malware, and hackers. Having a strong cybersecurity posture is critical for businesses to ensure the safety […]
The eight cybersecurity solutions I have listed below can be lifesavers from time to time. Although they may be static and old school, they are still worth using for cybersecurity. They will prevent 90% of current vulnerabilities and while they may make your life difficult, you will also benefit a lot. 1.VPN (IPsec, L2TP, openvpn, […]
This article is the second Cyber Security article, focused on IT Management concerns. On our first article Cyber Security 1: Establishing The Correct Security Policy, we explained the necessary five strategies to have a strict security policy. In this article, we continue with more technical cyber security recommendations. When you consider Cyber Security principles for your company, Zero Trust and Segmentation/Isolation are […]
The basic premise of search engine reputation management is to use the following three strategies to accomplish the goal of creating a completely positive first page of search engine results for a specific term…